背景
自建证书的时候,如果每个子域名都去申请次证书,会很麻烦,这个时候可以使用泛域名证书申请。
工具
acme
- 下载工具
curl https://get.acme.sh | sh
- 注册
acme.sh --register-account -m your_email@gmail.com
域名纳管在Cloudflare
- 查询自己
Cloudflare密钥,地址https://dash.cloudflare.com/profile/api-tokens,在其中找到Global Key,复制留存下来 - 设置环境变量
export CF_Key="your_gloal_key"
export CF_Email="your_email@gmail.com"
- 开始申请证书
acme.sh --issue -d "xxx.xyz" -d "*.xxx.xyz" --dns dns_cf --key-file /etc/nginx/ssl/xxx.key --fullchain-file /etc/nginx/ssl/xxx.pem --reloadcmd "systemctl restart nginx"
- 申请完成后,在
/etc/nginx/ssl下面应该已经有对应密钥
纯手搓
- 设置域名解析
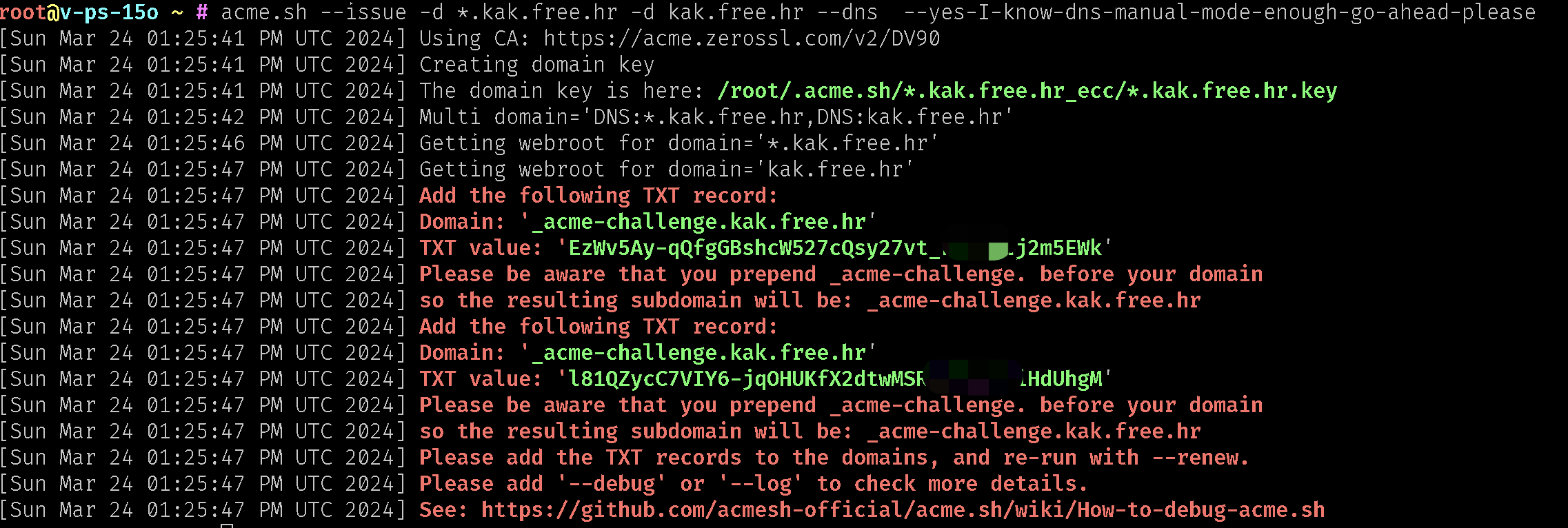
- 申请证书
acme.sh --issue -d *.kak.free.hr -d kak.free.hr --dns --key-file /etc/nginx/ssl/xxx.key --fullchain-file /etc/nginx/ssl/xxx.pem --yes-I-know-dns-manual-mode-enough-go-ahead-please
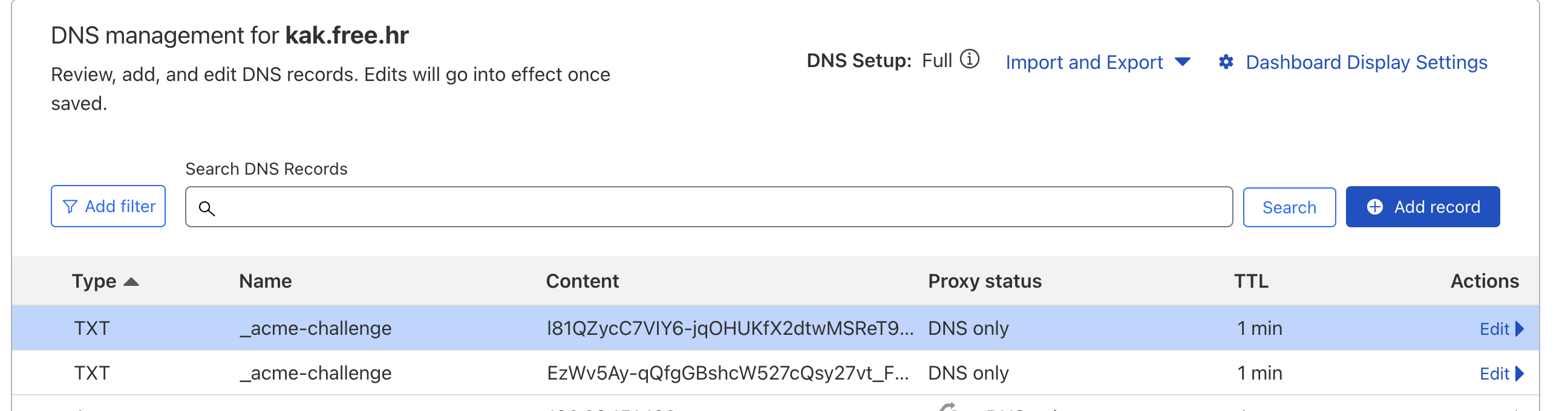
3. 在对应的域名纳管平台添加两条txt解析记录,如图
4. 等待一两分钟,执行
acme.sh --renew -d *.kak.free.hr -d kak.free.hr --dns --yes-I-know-dns-manual-mode-enough-go-ahead-please
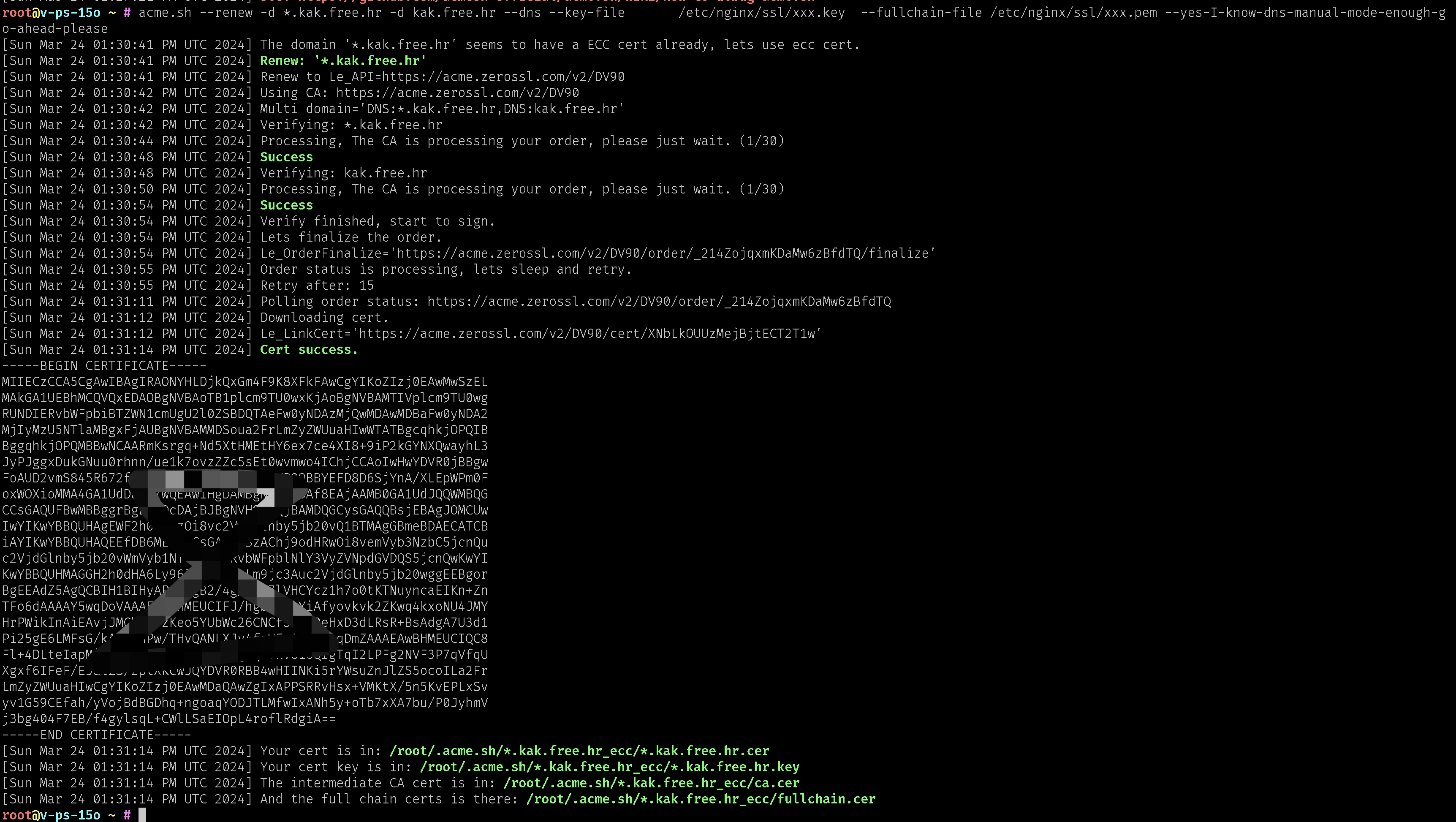
5. 从上面可以看到
[Sun Mar 24 01:31:14 PM UTC 2024] Your cert is in: /root/.acme.sh/*.kak.free.hr_ecc/*.kak.free.hr.cer
[Sun Mar 24 01:31:14 PM UTC 2024] Your cert key is in: /root/.acme.sh/*.kak.free.hr_ecc/*.kak.free.hr.key
[Sun Mar 24 01:31:14 PM UTC 2024] The intermediate CA cert is in: /root/.acme.sh/*.kak.free.hr_ecc/ca.cer
[Sun Mar 24 01:31:14 PM UTC 2024] And the full chain certs is there: /root/.acme.sh/*.kak.free.hr_ecc/fullchain.cer
将下面文件复制到/etc/nginx/ssl,修改443的配置
cat > /etc/nginx/conf.d/ssl.conf << EOF
server {
listen 443 ssl;
server_name test.kak.free.hr;
ssl_certificate /etc/nginx/ssl/fullchain.cer;
ssl_certificate_key /etc/nginx/ssl/*.kak.free.hr.key;
# 可选:配置SSL加密算法
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:...';
# 配置SSL会话缓存
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
# 其他HTTPS相关配置
# ...
client_max_body_size 10M;
location / {
proxy_pass http://127.0.0.1:80;
proxy_set_header X-Real-IP \$remote_addr;
proxy_set_header X-Forwarded-For \$proxy_add_x_forwarded_for;
proxy_set_header Host \$http_host;
}
}
EOF
- 重启nginx
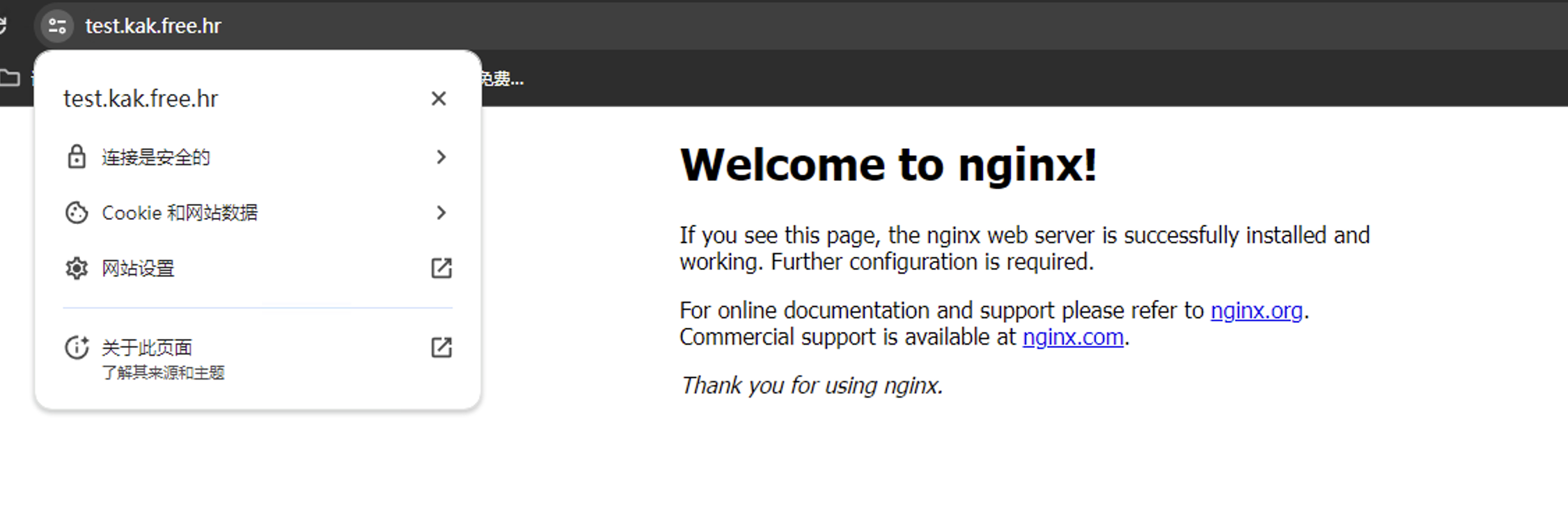
配置Nginx
- 在
/etc/nginx/conf.d/下面创建ssl.conf
cat > /etc/nginx/conf.d/ssl.conf << EOF
server {
listen 443 ssl;
server_name mon.xxx.xyz;
ssl_certificate /etc/nginx/ssl/181000.pem;
ssl_certificate_key /etc/nginx/ssl/181000.key;
# 可选:配置SSL加密算法
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:...';
# 配置SSL会话缓存
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
# 其他HTTPS相关配置
# ...
client_max_body_size 10M;
location / {
proxy_pass http://127.0.0.1:80;
proxy_set_header X-Real-IP \$remote_addr;
proxy_set_header X-Forwarded-For \$proxy_add_x_forwarded_for;
proxy_set_header Host \$http_host;
}
}
EOF
- 重启Nginx
systemctl restart nginx
或
nginx -s reload
- 访问对应域名的
https

重定向
当配置了https之后,可以将所有http请求都先重定向到https,在/etc/nginx/conf.d下面新建一个.conf结尾的文件即可
server {
listen 80 default_server;
server_name _;
return 301 https://$host$request_uri;
}